Tired of Online Stalkers? Here’s How to Hide Your Information Across the Internet. The internet has become an essential part of our daily lives, making tasks that once took hours or even days possible in just a few minutes. However, not everyone wants their real identity exposed online. Many people prefer to erase their digital footprint and keep their personal information private.
Unfortunately, removing your data from the internet isn’t as simple as pressing a delete button. However, by following specific steps, you can gradually reduce your online presence and protect your privacy.
Using Protective Techniques
Individuals, agencies, websites, and search engine algorithms collect your data through various methods, often using it for tracking and identification purposes.
To erase your digital footprint and understand how your data is gathered, it’s essential to familiarize yourself with two key concepts: OSINT and OPSEC.
OSINT refers to advanced search techniques used to gather publicly available information.
Cybercriminals and data brokers commonly use the following methods to access your data:
- Using search engines to find personal details shared online.
- Searching public records and stored databases to extract sensitive information.
- Encouraging users to create social media profiles and voluntarily share data.
- Tracking usernames by linking email addresses to online accounts.
- Analyzing images and videos posted on the internet.
Additionally, Geospatial Intelligence (GEOINT) is a subset of OSINT that involves searching satellite imagery and online maps to collect location-based data.
ALSO READ: Best Project Management Software Guide In 2025
OPSEC (Operational Security)
Now that you’re aware of key OSINT techniques, you can apply OPSEC (Operational Security) strategies to prevent unauthorized access to your personal data. In simple terms, any technique that reduces or eliminates your digital exposure falls under OPSEC.
Next, we’ll explore the most effective OPSEC techniques to help you safeguard your privacy.
🔷Using Encrypted Communication
Messaging apps like Signal, WhatsApp, and Telegram use end-to-end encryption (E2EE) to protect user conversations. With this technology, each message is encrypted in such a way that only the sender and the recipient can read it—no third party, including service providers, can intercept or decode the message during transmission.
🔷Removing Metadata from Images
Every photo you take with a camera, smartphone, or tablet contains metadata, which includes details about the location, device type, and other hidden information. This data can pose a privacy risk if shared publicly.
Some messaging apps, such as Telegram, automatically strip metadata from images before sending them. However, for complete control over metadata removal, tools like ExifTool can be used to delete location data and other embedded information from photos.
🔷Browsing the Internet Anonymously
To maintain anonymity while browsing, you can:
- Use private browsing mode in web browsers.
- Connect via a VPN (Virtual Private Network) to mask your IP address.
- Browse with privacy-focused browsers like Tor to prevent tracking and data collection.
These methods help protect your online identity and ensure a more private internet experience.
🔷Creating a Virtual Sandbox
For individuals engaging in high-risk activities or those requiring enhanced privacy, using a virtual machine (VM) or setting up a sandbox environment on Windows (or other operating systems) can help isolate internet activity from the main system. This reduces the risk of data leaks and identity exposure.
🔷Avoiding Online Engagement
To remain truly anonymous, it’s essential to minimize online interactions. This means:
- Avoiding likes, comments, and shares on social media.
- Reducing participation in public discussions.
- Limiting direct interactions with unknown individuals online.
By following these steps, you can reduce your digital footprint and keep your identity hidden from data collectors and cyber threats.
Removing Personal Information from the Internet
The second step to maintaining online anonymity is deleting personal information. This includes:
- Old or inactive user accounts
- Accounts containing real personal details (e.g., full name, phone number, email, workplace address)
- Photos and videos linked to your identity
To find out what information about you is publicly available, search for your full name (both in your native language and English) along with any personal details that might reveal your identity on Google or other search engines.
If you are willing to pay for specialized services, several platforms can help you track and erase your digital footprint. These services scan the web for your personal data and assist in removing it from various sources.
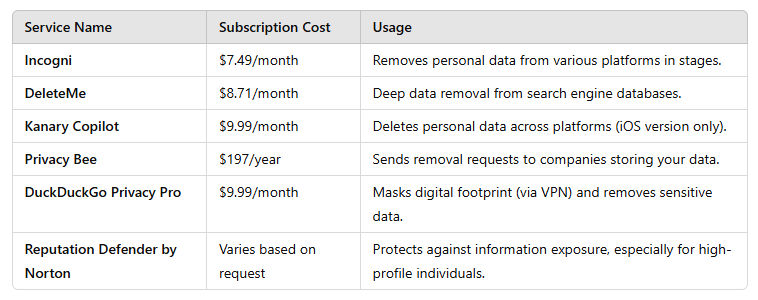
It’s essential to review your social media accounts and update your privacy settings to avoid being indexed by search engines.
If you don’t want your profile to be publicly visible, adjust your privacy and security settings. For example:
- Switch your account from Public to Private to limit who can see your posts.
- Restrict profile visibility so search engines can’t index your information.
- Remove personal details such as phone numbers, email addresses, and location data.
By doing this, you can minimize your online presence and reduce the chances of your information being found by unauthorized users or data brokers.
ALSO READ: Top 10 Programming Languages to Learn in 2025
Creating New and Anonymous Accounts
Once you have hidden your personal information from the internet, you have two options for maintaining online anonymity:
- Stop using the internet entirely.
- Create new anonymous accounts.
Since the first option isn’t practical in today’s digital world, the second option is the better choice. If you decide to proceed with this method, the first step is to stop using your old email and create a new, anonymous email account for signing up on websites and services.
Instead of registering with mainstream providers like Gmail or Yahoo, consider privacy-focused email services that prioritize security. Here are some of the best options:
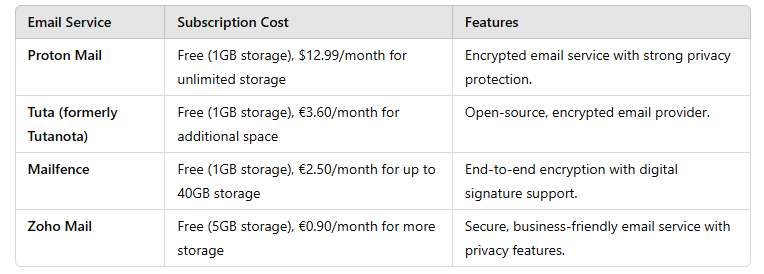
By using privacy-focused email services, you can avoid tracking and enhance your online security while creating new accounts.
If you want to stay completely anonymous, use a VPN when signing up for these email services. Preferably, access your email account from a virtual machine for added security.
Creating Misleading Content to Confuse Search Engine Algorithms
Instead of deleting your online accounts, you can mislead search engines and data collectors by replacing your real personal details with random or false information.
By doing this:
- Anyone searching for your information will be misled by incorrect details.
- Search engine algorithms will index and display false data instead of your real identity.
- Over time, repeated searches for the misleading information will cause search engines to associate your profile with the false details, reducing the visibility of your real data.
This strategy helps protect your privacy while keeping your accounts active without exposing personal information.
This approach requires time and consistency. You need to gradually add misleading information to your selected accounts to make it effective.
If you’re looking for faster results, it’s best to rely on previous methods, such as deleting personal data or using privacy-focused services.


Leave a Reply